Massive NPM Supply-Chain Attack Targets ENS-Linked Libraries in Shai Hulud Breach
A massive JavaScript-based Node Package Manager (npm) supply-chain attack has infiltrated code libraries connected to the Ethereum Name Service (ENS) and hundreds of older software packages, with over 10 widely used across the crypto ecosystem, according to cybersecurity firm Aikido Security.
Charlie Eriksen, a malware researcher at the security firm, disclosed that the supply-chain malware known as “Shai-Hulud: The Second Coming” has infected hundreds of packages and more than 25,000 GitHub repositories.
According to the findings, threat actors have embedded this malicious code into over 490 npm packages with more than 132 million monthly downloads, including prominent ones from ENS, Zapier, AsyncAPI, Browserbase, and Postman.
“If a developer installs one of these bad packages, the malware quietly runs during installation, before anything even finishes installing,” Eriksen said.
How the Shai-Hulud Supply-Chain Malware Works
As described by Akido security, the Shai-Hulud malware gains access to the developer’s machine or cloud environment during installation.
It then deploys an automated tool called TruffleHog to scan for sensitive data, including passwords, API keys, cloud tokens, and GitHub or NPM credentials.
Any discovered information is then uploaded to a public GitHub repository titled “Shai-Hulud: The Second Coming.”
If the stolen credentials include access to code repositories or package registries, attackers can leverage them to breach additional accounts and distribute more malicious packages, allowing the attack to propagate further.
Evolution from September’s Attack
The initial Shai-Hulud breach occurred in early September, marking the largest npm attack on record at the time, with hackers stealing $50 million in cryptocurrency.
Ledger hardware wallet noted that this first attack was followed by the Shai Hulud worm spreading autonomously a week later.
However, the infiltration method for this second wave appears substantially different.
The “Shai-Hulud: The Second Coming” first installs Bun via the file setup_bun.js, then uses it to execute bun_environment.js, which contains the actual malicious code.
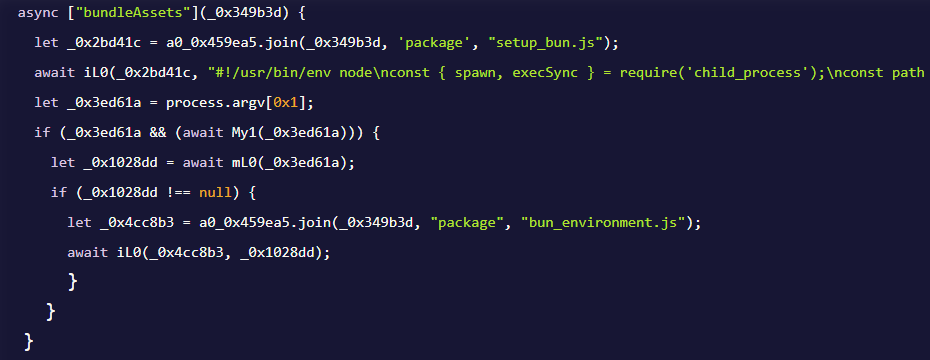 Source: Aikido Blog
Source: Aikido Blog
It creates randomly named repositories with stolen data rather than using hardcoded names, and can infect up to 100 npm packages compared to 20 in the previous attack.
Self-Propagating Malware Exposes Blind Spot in NPM Packages
Charles Guillemet, Chief Technology Officer at crypto hardware wallet Ledger, alerted the community that the malware also targets API keys, Git credentials, and CI/CD secrets, then quietly exfiltrates everything.
“If you use affected packages: PLEASE check this carefully: consider your credentials and secrets compromised, audit your infrastructure, and rotate your credentials,” he cautioned.
He urged that anyone without close CI monitoring might consider shutting down their systems.
Florian Roth, Head of Research at Nextron Systems, also added that it’s becoming increasingly easy for threat actors to inject malware into sensitive systems due to blind spots in NPM packages.
According to his assessment, the industry previously fought malware at the OS level, but now the same behavior occurs one layer up, inside the software ecosystems people trust every day.
“NPM tokens, transitive deps, weak account hygiene, zero visibility… and suddenly a self-propagating worm runs through the supply chain like it’s 2003 again.”
He concluded that the recent Shai Hulud breach reveals the real blind spot is in package ecosystems acting as execution surfaces.
“Nobody monitors them, nobody hardens them, and attackers don’t even need an exploit to make them go wild,” he said.
JP Richardson, CEO of Exodus, the first public company in the U.S. to tokenize stocks on the blockchain, also questioned Microsoft for making it “easy” for threat actors to propagate malware.
In a November 24 post, Richardson said, “What I don’t understand [is] why Microsoft (npm owner) is not moving fast enough to detect these attacks.”
He believes any package that has a pre-install or post-install script added should display warnings to everyone on the npm site and before package installation.
Ayrıca Şunları da Beğenebilirsiniz

The Channel Factories We’ve Been Waiting For

SOLANA NETWORK Withstands 6 Tbps DDoS Without Downtime
