1) Lit Protocol combines threshold MPC and TEE technologies to deliver decentralized and programmable key management, addressing a critical gap in the Web3 infrastructure stack.
2) The Lit Actions feature allows developers to embed complex business logic into the signing process, enabling conditional execution and WASM for unprecedented flexibility in automated transactions.
3) The LITKEY token secures the network through staking, pays for service fees, and facilitates protocol governance, creating a self-sustaining economic system.
4) The Vincent framework provides fine-grained permission controls for AI agents, solving the trust challenge of safely managing user assets.
5) The Lit Protocol ecosystem already spans multiple domains, including cross-chain interoperability, user data sovereignty, and DeFi. It manages over $154 million in assets and serves more than 1.4 million wallets.
As a decentralized key management network, Lit Protocol not only fills a crucial gap in the Web3 technology stack but also empowers developers with programmable signing and encryption capabilities. By transforming key management into a programmable computational primitive, Lit Protocol is redefining how we think about digital asset security, data privacy, and cross-chain interoperability.
Lit Protocol is a decentralized key management network that provides programmable signing and encryption capabilities. It enables developers to build secure decentralized applications that can seamlessly manage digital assets, private data, and user permissions across platforms.
Lit's threshold cryptography architecture ensures that keys remain verifiably secure. At the hardware layer, it enforces physical isolation and cryptographic protection, while key shares are distributed and stored across the decentralized network. This represents the first time developers can programmatically control universal accounts without relying on a centralized custodian. Through the Lit SDK, developers can easily implement data encryption, create and manage Web3 accounts, generate digital signatures, execute blockchain transactions, and perform virtually any signing or encryption task.
These capabilities empower developers to build tamper-proof, interoperable applications, agents, and protocols that give users full control. Existing use cases within the Lit ecosystem already include AI-powered agents, cross-chain DeFi solutions, general-purpose solvers, user-sovereign private accounts, and decentralized data marketplaces.
LITKEY is the native token of Lit Protocol. According to the official documentation, LITKEY serves multiple roles simultaneously: it functions as a work token, a payment token, and a governance token. It secures the Lit Protocol network, pays for network services, and enables holders to participate in on-chain governance that shapes the network's future.
LITKEY will be introduced ahead of the launch of the Lit v1 mainnet, known as Naga. During its initial phase, the token will be distributed through an airdrop to qualified participants, including early adopters, ecosystem builders, testnet node operators, and other community members. The airdrop will place particular emphasis on rewarding ecosystem contributors, with additional allocations for users who take part in The Ciphernaut's Path, a series of missions designed to explore and engage with the Lit Protocol ecosystem.
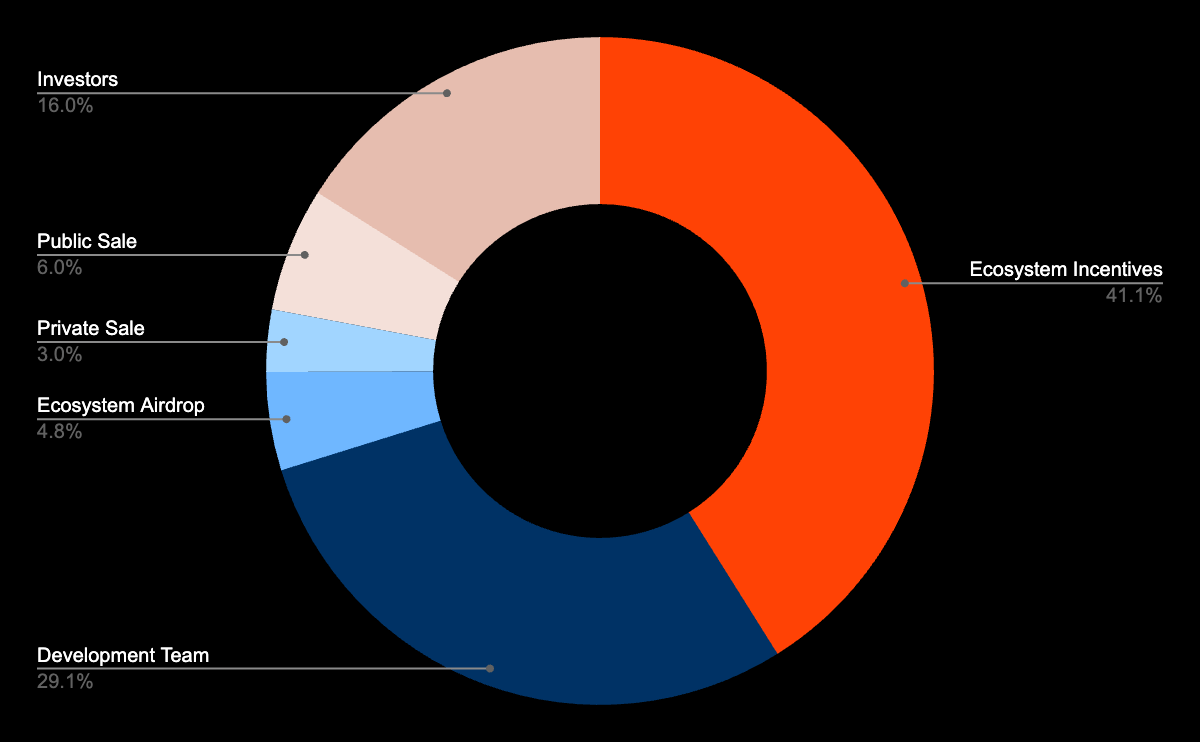
Allocation Category | Description | Lock-up/Vesting Mechanism |
Investors | Tokens allocated to Lit investors | Locked for 1 year after TGE, followed by linear vesting over 4 years |
Team | Tokens reserved for the Lit Protocol development team | Locked for 1 year after TGE, followed by linear vesting over 4 years |
Ecosystem Airdrop | Tokens distributed to ecosystem builders, testnet node operators, integration partners, and task participants | - |
Public and Private Sale | Tokens allocated for public sale and community sale | - |
Ecosystem Incentives | Tokens used for grants, node rewards and incentives, ecosystem growth programs, and ongoing protocol development | - |
1) Work Token: Securing the Network and Incentivizing Service Providers
The primary role of LITKEY is to function as a work token, serving both to safeguard the network and to compensate protocol participants.
Staking Mechanism:
Node operators are required to stake LITKEY in order to participate in the Lit network.
Staking represents an economic commitment, signaling the operator's reliability and long-term support for network security.
This ensures that operators remain incentivized to maintain uptime, correctly execute cryptographic tasks, and adhere to protocol rules.
Reward Distribution:
LITKEY is used to compensate node operators who run the core Lit Protocol software.
Operators earn rewards for performing signing, encryption, and computation tasks.
Token rewards are allocated based on each operator’s relative contribution to the network.
2) Payment Token: Covering Network Service Fees
LITKEY also functions as a service payment token, similar to gas, facilitating both on-chain and off-chain operations within the Lit ecosystem.
Use Cases:
Paying for network services such as signing, encryption, and computation operations.
Allowing users and applications to pay per operation, ensuring efficient allocation of network resources.
Serving as the native token for Lit Protocol's blockchain components, enabling on-chain activities such as generating new key pairs or staking.
3) Protocol Governance
As the governance token of the Lit Protocol ecosystem, LITKEY enables holders to guide the protocol's development through decentralized on-chain governance.
Governance Powers:
Token holders play a central role in selecting network operators.
They can influence partnerships, integrations, and network expansion initiatives that drive ecosystem growth.
Governance mechanisms will continue to evolve as the protocol matures.
At the heart of Lit Protocol's technology lies Threshold Multi-Party Computation (Threshold MPC). This advanced cryptographic technique ensures that a private key never exists in its entirety on a single node. Instead, the key is divided into multiple fragments (key shares), which are distributed across different nodes in the network. A signing or decryption operation can only be executed once a predefined threshold of nodes reaches consensus.
This design provides a groundbreaking level of security: even if a subset of nodes is compromised, an attacker cannot reconstruct the full private key. Equally important, the entire process is transparent and verifiable, giving users confidence that their keys remain secure at all times.
To further strengthen security, Lit Protocol combines Trusted Execution Environment (TEE) technology with MPC in an innovative way. Every network node operates within a TEE, providing hardware-level isolation and cryptographic protection. Even if a node's operating system is fully compromised, the computations and data processed inside the TEE remain secure.
This "defense-in-depth" strategy means that an attacker would need to simultaneously bypass multiple independent layers of security to pose any threat to the system, a scenario that is practically impossible in real-world conditions.
As the network expands, traditional MPC systems often encounter performance bottlenecks. Lit Protocol addresses this challenge through the introduction of Shadow Splicing, a novel technique that enables near-linear scalability while maintaining security. When demand surges, the network can scale horizontally in real time without compromising either security or performance.
Lit Actions is one of the most innovative features of Lit Protocol. It allows developers to embed complex business logic directly into the signing process. In this model, a key is no longer just a simple "on/off switch" but rather an intelligent executor capable of making decisions based on predefined conditions.
For example, a developer can design a Lit Action that only executes a signature if it occurs within a specific time window, falls within a certain transaction amount, or meets defined on-chain conditions. This capability introduces unprecedented flexibility for use cases such as automated trading, conditional payments, and multi-signature wallets.
Lit Actions already supports WebAssembly (WASM), which means developers can write complex logic in any programming language and have it securely executed within the decentralized network.
Lit Protocol's encryption capabilities go far beyond traditional static encryption. By leveraging Access Control Conditions (ACCs), data owners can precisely define who can decrypt their data and under what circumstances. These conditions may be based on:
On-chain state (e.g., holding a specific NFT or maintaining a certain token balance)
Temporal rules (e.g., data becomes decryptable only after a certain date)
Multi-party authorization (e.g., requiring approval from multiple participants)
Combinations of complex business logic
This flexibility enables the creation of user-owned data marketplaces, privacy-preserving DeFi applications, and encryption solutions designed to meet regulatory compliance requirements.
Vincent is a groundbreaking framework built on top of Lit Protocol, designed specifically to provide secure key management and permission controls for AI Agents. As AI Agents continue to evolve rapidly, a central challenge has emerged-how to enable them to manage user assets safely.
Vincent addresses this challenge by offering fine-grained permission controls. Users can precisely define the scope of an agent's operations, such as:
This design empowers users to fully leverage the automation capabilities of AI Agents while maintaining ultimate control over their assets.
Lit Protocol's universal account functionality fundamentally transforms the paradigm of cross-chain interaction. By introducing a unified key management layer, developers can create true "omnichain accounts" that seamlessly operate across any blockchain network, including Bitcoin, Ethereum, Solana, and Cosmos. Practical applications include:
Emblem Vault: Smart vaults capable of autonomously executing cross-chain operations.
Genius Bridge Protocol: A cross-chain liquidity solution that eliminates the need for centralized relayers.
Tria: An intent-driven, wallet-agnostic payment primitive.
Several projects are leveraging Lit Protocol to build a data layer that is truly controlled by users:
Verify (Fox Corp): Provides verifiable access control for media content.
Streamr: Develops a decentralized data streaming network.
Beacon Protocol: Creates a private data layer that enables AI models to securely access user information.
Together, these applications highlight a new vision for the internet, where data is stored on open networks but access rights remain entirely under the control of the user.
Lit Protocol is more than just a technical protocol. It represents an important step forward in the evolution of internet infrastructure. By transforming key management and cryptographic operations into programmable network services, Lit Protocol unlocks new possibilities for developers.
Whether it is powering autonomous AI Agents, enabling true cross-chain interoperability, or creating user-owned data marketplaces, Lit Protocol provides the essential infrastructure to make it possible. As the Web3 ecosystem continues to mature, decentralized key management will become a core requirement for an increasing number of applications.
Disclaimer: This material does not constitute advice on investments, taxes, legal matters, finance, accounting, consulting, or any other related services, nor is it a recommendation to buy, sell, or hold any assets. MEXC Learn provides information for reference only and does not constitute investment advice. Please ensure you fully understand the risks involved and invest cautiously. All investment decisions and outcomes are the sole responsibility of the user.